What is Secure Hashing Algorithm (SHA)?
Secure Hashing Algorithm is an algorithm developed by NIST (National Institute of Standards and Technology) and other government agencies to provide better online security standards. It is a family of cryptographic hash functions designed to keep your data secure. It works by taking an input of arbitrary size and converts it into the fixed-sized output. E.g. SHA-1 takes any input of size < 2^64 bits and produces an output of 160 digit hex values. Similarly, SHA-256 takes an input size < 2^64 bits and produces an output of 256 digit hex values.
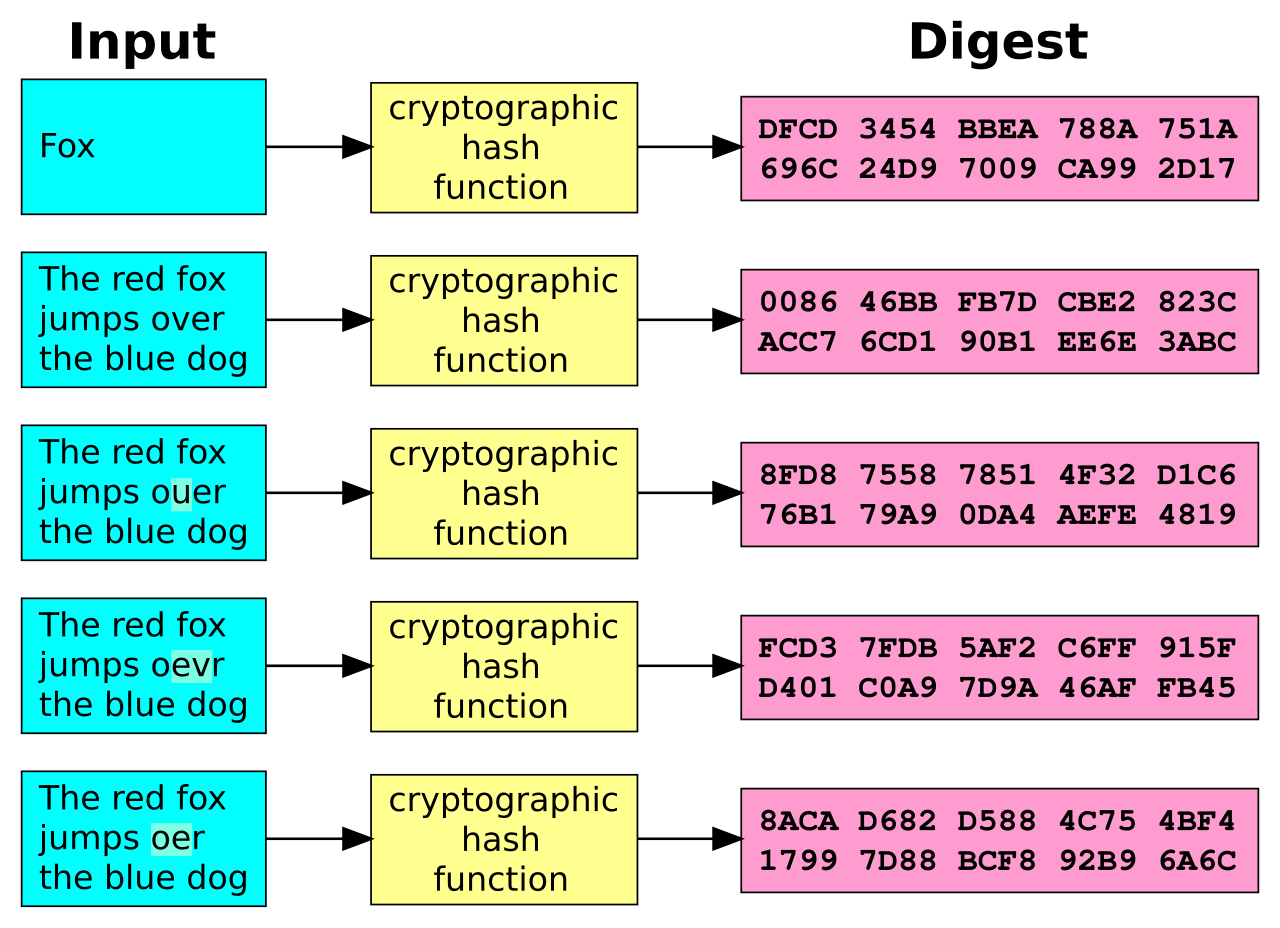
SHA is designed to be a One-way function, meaning once the input is converted into hash value, it’s nearly impossible to get back the original data. SHA also follows avalanche effect, which means a small change in input causes a drastic change in the output digest; conversely, the drastically different inputs may have same hash value.
SHA algorithms consist of bitwise operations, arithmetic operations, and compression functions to produce the hash values. SHA algorithms follow some fundamental safety characteristics such as Pre-image resistance and Collision resistance. Pre-image resistance feature wards off brute force attack on your data. It basically means reversing the algorithm to get back your password is nearly impossible. Collision resistance makes it extremely difficult to find two messages that have same hash value.
SHA is used by companies to secure your password. As soon as you enter your password on any website, it gets converted into its corresponding hash value and this hash value is stored by the companies in their databases. So, if in any case the database gets hacked, hackers will only find the hash value of your password and not the actual password. Now, due to the algorithm complexity, it’s impossible for hackers to get your original password. In case you think, What if attackers could input the hash value of your password and get access? The answer to this question is No, if attackers try to input the hash value then it’s treated as an input string which is again converted into a different hash value.
SHA is also used to validate files, Software’s, Games, videos, etc. Almost every Company produces an SHA digest for its users to verify their respective downloads. You can find the SHA-2 value somewhere around the link provided to download the file. You can produce the SHA-2 value of the downloaded file by using any software available online than you can match both the hash values, one provided on the website and other produced by you. This is extremely useful to check if your download was tampered in between.
How to validate files, you download from the internet?
- Download and run MD5 and SHA Checksum Utility.
- Browse to the location of the file, you need to verify.
- The MD5 and SHA Checksum utility will automatically run and produce all the hash values like MD5, SHA-1 and SHA-255.
- Paste the SHA or MD5 hash value from the website to the utility.
- Click on verify.
You should verify every software or file, you download from the internet.
I hope this information helps. Please comment down below, If you come up with any queries or suggestions. Finally, Thank you.
I hope this information helps. Please comment down below, If you come up with any queries or suggestions. Finally, Thank you.

No comments:
Post a Comment